nginx-pod.yaml
apiVersion: v1
kind: Pod
metadata:
name: nginx-pod
spec:
containers:
- name: nginx
image: nginx


Private Repository
$ docker login private-registry.io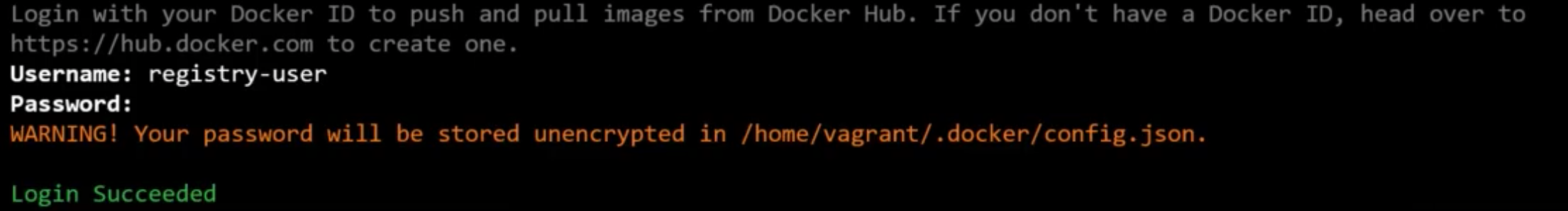
$ docker run private-registry.io/appsinternal-app
nginx-pod.yaml
apiVersion: v1
kind: Pod
metadata:
name: nginx-pod
spec:
containers:
- name: nginx
image: private-registry.io/appsinternal-app
How do you pass the credentials to the docker on time on the worker node for that we first create a secret object with the credentials in it
kubectl create secret docker-registry regcred \
--docekr-server= private-registry.io \
--docker-username= registry-user \
--docker-password= registry-password \
--docker-email= registry-user@org.com \
apiVersion: v1
kind: Pod
metadata:
name: nginx-pod
spec:
containers:
- name: nginx
image: private-registry.io/appsinternal-app
imagePullSecrets:
- name: regcred[Practice Test]
ㅁ We have an application running on our cluster. Let us explore it first. What image is the application using?
$ kubect get deployment
NAME READY UP-TO-DATE AVAILABLE AGE
web 2/2 2 2 7m1s$ kubectl describe deployment web
Name: web
Namespace: default
CreationTimestamp: Tue, 30 Mar 2021 10:58:45 +0000
Labels: app=web
Annotations: deployment.kubernetes.io/revision: 1
Selector: app=web
Replicas: 2 desired | 2 updated | 2 total | 2 available | 0 unavailable
StrategyType: RollingUpdate
MinReadySeconds: 0
RollingUpdateStrategy: 25% max unavailable, 25% max surge
Pod Template:
Labels: app=web
Containers:
nginx:
Image: nginx:alpine
Port: <none>
Host Port: <none>
Environment: <none>
Mounts: <none>
Volumes: <none>
Conditions:
Type Status Reason
---- ------ ------
Available True MinimumReplicasAvailable
Progressing True NewReplicaSetAvailable
OldReplicaSets: <none>
NewReplicaSet: web-bd975bd87 (2/2 replicas created)
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal ScalingReplicaSet 6m41s deployment-controller Scaled up replica set web-bd975bd87 to 2ㅁ We decided to use a modified version of the application from an internal private registry. Update the image of the deployment to use a new image from myprivateregistry.com:5000
kubectl edit deployment webapp
image: myprivateregistry.com:5000/nginx:alpine
으로 수정ㅁ Are the new PODs created with the new images successfully running?
[NO]
ㅁ Create a secret object with the credentials required to access the registry
- Name: private-reg-cred
- Username: dock_user
- Password: dock_password
- Server: myprivateregistry.com:5000
- Email: dock_user@myprivateregistry.com
kubectl create secret docker-registry private-reg-cred \
--docker-username=dock_user \
--docker-password=dock_password \
--docker-server=myprivateregistry.com:5000 \
--docker-email=dock_user@myprivateregistry.comㅁ Configure the deployment to use credentials from the new secret to pull images from the private registry
kubectl edit deployment web
kubectl edit deployment web
아래 부분 수정
spec:
containers:
- image: myprivateregistry.com:5000/nginx:alpine
imagePullPolicy: IfNotPresent
name: nginx
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
dnsPolicy: ClusterFirst
imagePullSecrets:
- name: private-reg-cred
'CKA &. CKAD > Security' 카테고리의 다른 글
| Network Policy (0) | 2021.03.30 |
|---|---|
| Practice Test - Security Contexts (0) | 2021.03.30 |
| Cluster Roles (0) | 2021.03.29 |
| RBAC (Role Based Access Controls) and Practice Test (0) | 2021.03.29 |
| Authorization (0) | 2021.03.29 |



