RDS and CloudFormation
- AWS::RDS::DBInstance
- https://docs.aws.amazon.com/ko_kr/AWSCloudFormation/latest/UserGuide/aws-properties-rds-database-instance.html
AWS::RDS::DBInstance - AWS CloudFormation
If any value is set in the Iops parameter, AllocatedStorage must be at least 100 GiB, which corresponds to the minimum Iops value of 1,000. If you increase the Iops value (in 1,000 IOPS increments), then you must also increase the AllocatedStorage value (i
docs.aws.amazon.com
- Important Parameters:
- DeleteAutomatedBackups: remove automated backups immediately after the DB instance is deleted. Default value: remove all automated backups
- DeletionProtection: enable protection on the DB in RDS. The database can't be deleted while it has DeletionProtection on.
- MasterUsername / MasterPassword: must be provided as text values (we'll see how to handle that securely later on)
- EnableIAMDatabaseAuthentication: can be enabled, does not replace Master username & password
- DBClusterIDentifier: (optional) if the DB belongs to an Aurora DB cluster
RDS and CloudFormation - DB Updates
- If Update Requires:Replacement:
- New DB is created
- Links are updated
- Old DB is deleted
- If a DB instance is deleted or replaced during an update, AWS CloudFormation deletes all automated snapshots.
- However, it retains manual DB snapshots
- During an update that requires replacement, you can apply a stack policy to prevent DB instances from being replaced
RDS and CloudFormation - database update
- Take a snapshot before updating an update. If you don't, you lose the data when AWS CloudFormation replaces your DB instance.
To preserve your data:
- Deactivate any applications that are using the DB instance so that there's no activity on the DB instance.
- Create a snapshot of the DB instance
- If you want to restore your instance using a DB snapshot, modify the updated template with your DB instance changes and add the DBSnapshotIdentifier property with the ID of the DB snapshot that you want to use.
- After you restore a DB instance with a DBSnapshotIdentifier proeprty, you must specify the same DBSnapshotIdentifier property for any future updates to the DB instance.
- Update the stack.
- DBSnapshotIdentifier is also useful for mass creating dev/test databases with some data from prod
CloudFormation protections
- CloudFormation Stack Termination Protection: can't delete the stack without removing it (but you can still update the stack)
- CloudFormation Stack Policy: prevent updates to CloudFormation templates.
- CloudFormation DeletionPolicy: what happens if a resource gets deleted
- Delete: delete the resource (default behaviour for most resources)
- Retain: do not delete the resources
- Snapshot: (onlyt to resources that support snapshot) snapshot then delete
- The default CloudFormation behavior for RDS depends on DBClusterIdentifier:
- IF DBClusterIdentifier not specified (=non Aurora), CloudFormation will snapshot
- If DBClusterIDentifer is specified (=Aurora), CloudFormation delete the DB Instance
Aurora with CloudFormation

- First create an AWS::RDS::DBCluster
- Then add AWS::RDS::DBinstance
- Default DeletionPolicy of RDS::DBCluster is Snapshot
- Means if individual DBInstance are deleted, no snapshot is made (default)
- If the DBCluster is deleted, a snapshot will be made
- RDS::DBInstance will inherit configurations
CloudFormation Parameters

- Parameters are referenced using !Ref
- They can have 4 different sources:
- (static) Given using the CLI / Management console
- (static) Given using a flat file from local filesystem or S3
- (dynamic) From the SSM Parameter Store
- (dynamic) From AWS Secret Manager
- The last two are the most secure way
- Exam trap: you cannot pass in KMS encrypted parameters through
- Use SSM Parameter Store or Secrets Manager instead!
CloudFormation Parmeters - SSM

- Retrieve a String (plaintext) or SecureString (KMS encrypted) from SSM Parameter Store at runtime!
- Amazing to s t ore environment specific variables
- Hierarchical way of storing parameters
- SSM CF parameters: will be resolved every time you run the template, does not work for SecureString.
- Dynamic parameter pattern:
'{{resolve:ssm:parameter-name:version}}', you must specify the exact version, works for SecureString.
CF Parameters - Secrets Manager

- Secrets rotation + integration with RDS =
- Dynamic parameter pattern:
'{{resolve:ssm:parameter-name:version}}', you must specify the exact version - Neither Secrets Manager nor CloudFormation logs or persists any resolved secret value
- Updating a secret in Secrets Manager does not automatically update the secret in CloudFormation
- To manage updating the secret in your template, consider using version-id to specify the version of your secret - {{resolve:secretsmanager:secret-id:secret-string:json-key:version-stage:version-id}}
Secrets Manager + RDS

1. Create a AWS::SecretsManager::Secret
- Specify GenerateSecretString to randomly generate a secret
2. Create an AWS::RDS::DBInstance that references that secret
- Using dynamic references
3. Create a AWS::SecretsManager::SecretTargetAttachment
- Link to Secrets Manager secret and the RDS database together
- Will add RDS properties to Secret Manager JSON
Secrets Manager Rotation Schedule
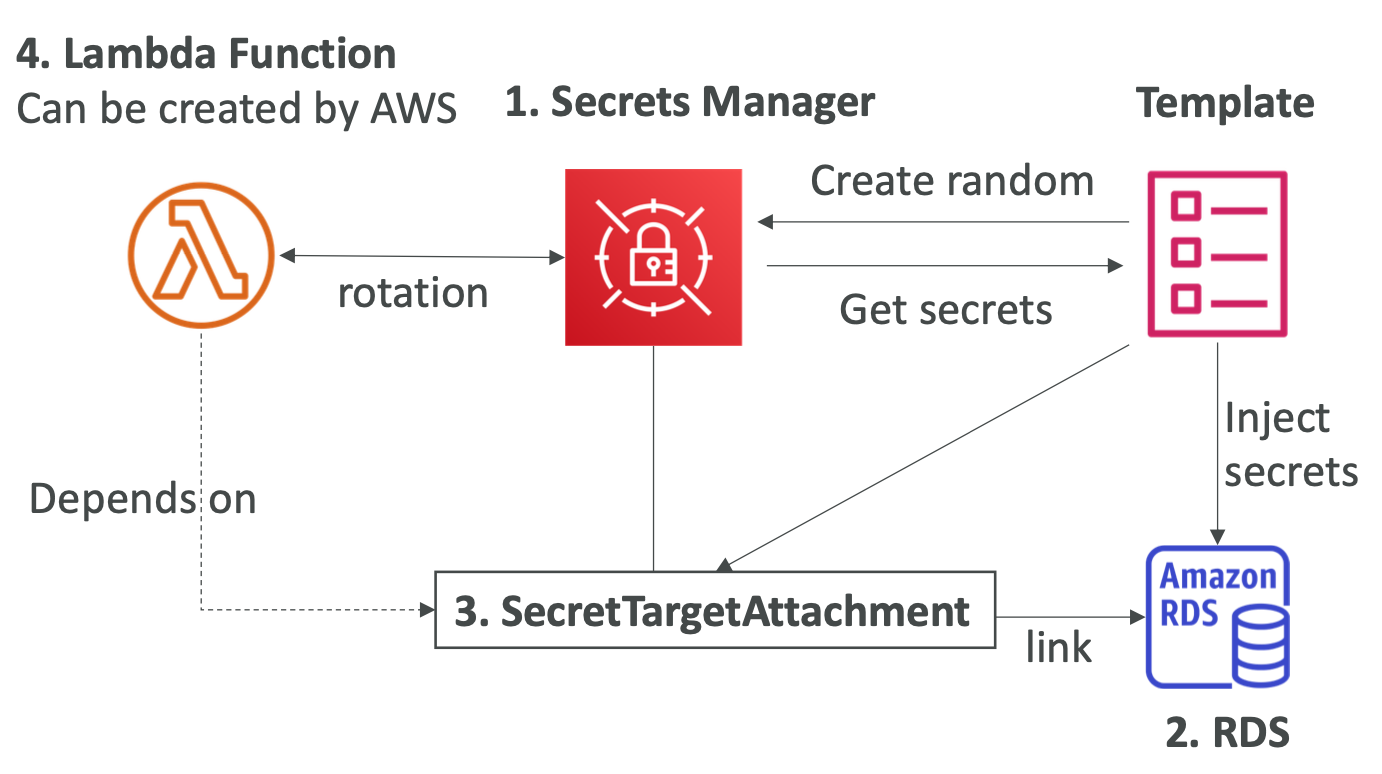
4. Create a AWS::SecretsManager::RotationSchedule
- It will create a Lambda function
- You must do this after creating the secret attachment
Other CloudFormation concepts
- CloudFormation Drift:
- See if the resource configurations have changed from the template over time
- Stack Set:
- Apply the same CloudFormation template into many accounts / regions
- Change Set:
- Evaluate the changes that will be applied before applying them (safety)