A certificate is used to guarantee trust between two parties during a transaction

Scenario






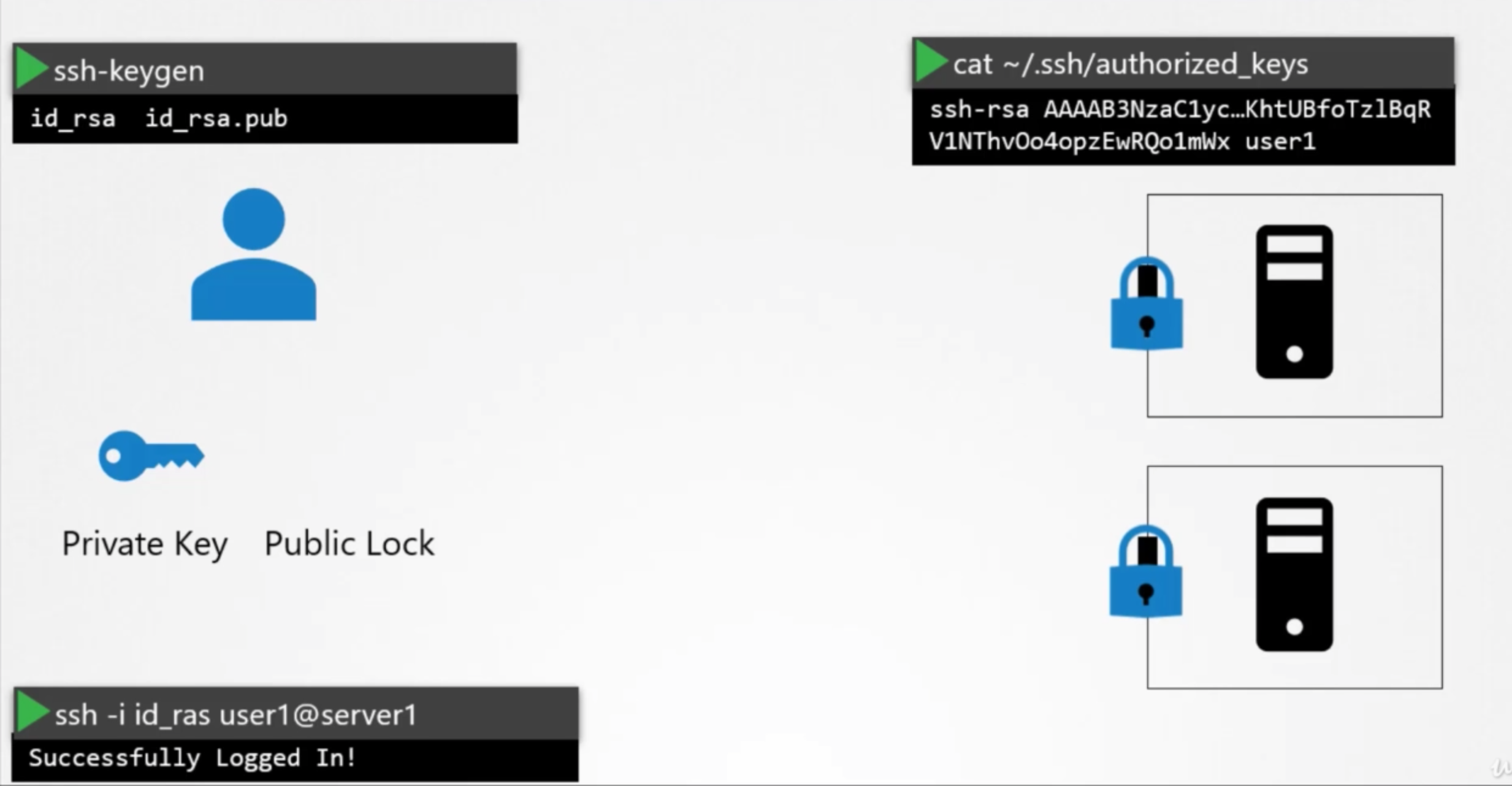

we're going to refer to the public lock as public key going forward now that you have got the idea that the ssh-keygen command we used earlier create a pair of keys for SSH purposes. so the format is bit different

here we use the openssl command to generate a private and public key pair. and that's how they look.

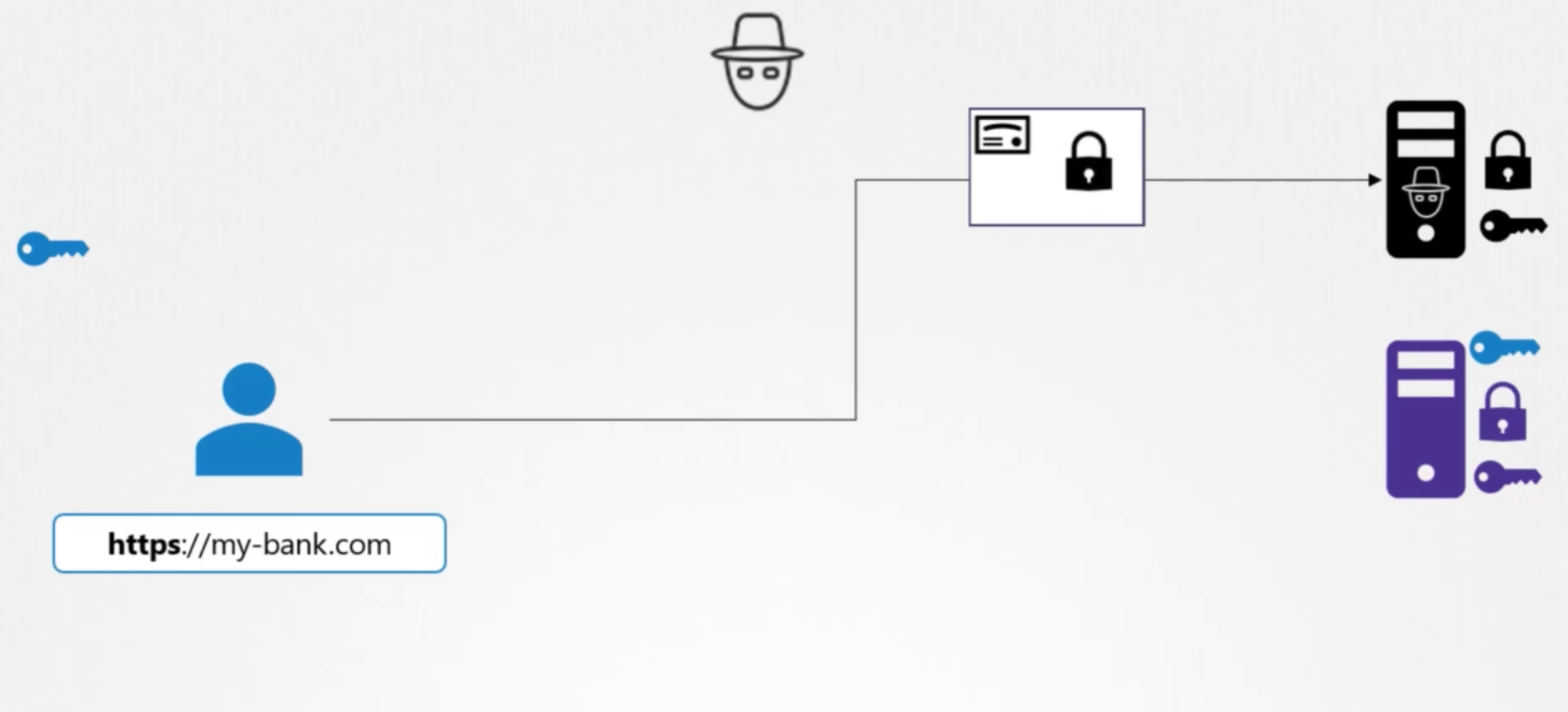
when the user first accesses the web server using https,

he gets the public key from the server since the hacker is sniffing all traffic that is assumed he too gets a copy of public key.
In fact the user's browser then encrypts the symmetric key using the public key provided by the server

The symmetric key is now secure the user then sends this to the server

The hacker also gets a copy the server uses the private key to decrypt the message and retrieve the symetric key froim it

However the hacker does not have the private key to decrypt and retrieve the symmetric key from the message. it received the hacker only has the public key with which he can only lock or encrypt a message and not decrypt the message the symmetric key is now safely available only to the user and the server

it received the hacker only has the public key with which he can only lock or encrypted message and not decrypt the message the symmetric key is now safely available only to the user and the server

they can now use the symmetric key to encrypt data and sent to each other the receiver can use the same symmetric key to decrypt data and retrieve information

The hacker is left with the encrypted messages and public keys with which he can decrypt any data with asymmetric encryption.
The hacker now looks for new ways to hack into our account and so he realizes that the only way he get your credential is by getting you to type it into a form he presents.

so he create a web site that looks exactly like your bank's web site. the design is the same, graphic is the same.

The web site is a replica of the actual bank's Web site.

He hosts the website on his own server

so he generates his own set of public and private key pairs and configure them on his web server. and finally he somehow manages to weak you environment or your network to route your request going to your bank's web site to his servers.

when you open up your browser and type the website address in you see a very familiar page the same login page of your bank that you're used to see so you go ahead and type in the username and password. You made sure you type in HTTPS in the URL to make sure that communication is secure encrypted your browser receives the key you send encrypted.





If you take a closer look at the certificate you will see that is is like an actual certificate. but in a digital format it has information about who the certificate is issued to the public key of that server the location of that server etc.

on the right you see the output of an actual certificate
every certificate has a name on it the person or subject to whom the certificate is issued to.
That is very important as that is the field that helps you validate their identity.
If this is for a web server this must match what the user type in the you are on his browser. If the bank is known by any other names and if they like their users to access their application with the other names as well then all those names should be specified in the certificate under the subject
Who Sign?










'CKA &. CKAD > Security' 카테고리의 다른 글
| Practice Test - Certificates API (0) | 2021.03.29 |
|---|---|
| Practice Test - View Certificates (0) | 2021.03.29 |
| TLS Certificates (0) | 2021.03.29 |
| TLS in Kubernetes (0) | 2021.03.29 |
| Authentication (0) | 2021.03.28 |


